Following the reveal of the Foreshadow (L1TF) Intel CPU flaw, as well as the previous TLBleed flaw, Theo de Raadt, founder of OpenBSD, which makes a free, multi-platform, UNIX-like operating system, recommended everyone completely disable Intel’s Hyper-Threading in BIOS before hackers start taking advantage of it.
Hyper-Threading Is Unsafe
In a post this week, de Raadt said that the Foreshadow and TLBleed flaws have made it mandatory to disable the Hyper-Threading technology on all Intel-based machines. He claimed mitigating these flaws requires a new CPU microcode and coding workarounds, but these alone are not sufficient to stop attackers; Hyper-Threading also has to be disabled.
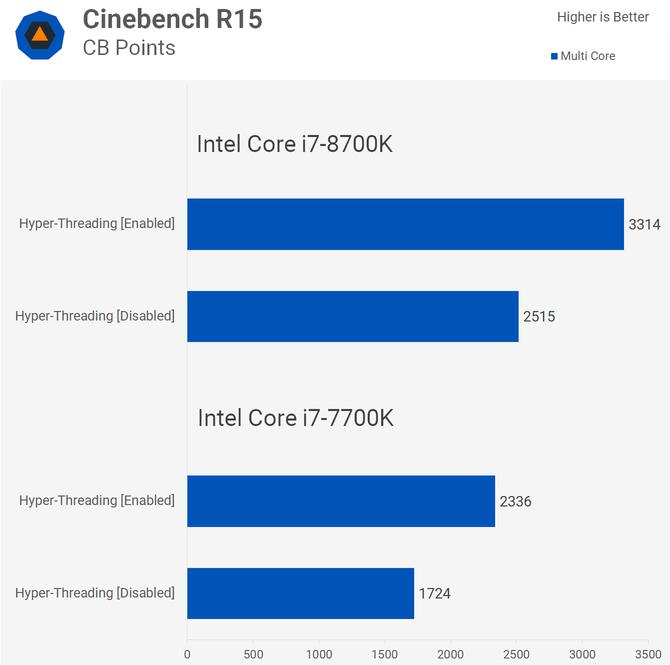
Hyper-Threading, which is Intel’s brand name for the simultaneous multithreading technology, is fundamentally broken, according to the OpenBSD founder. The technology enables the CPU to share resources that lack security differentiators.
The side-channels attacks enabled by this vulnerability are not easy to implement, but he believes that eventually attackers will find a way to make them work reliably in order to leak kernel or cross-VM memory in common usage circumstances, such as using JavaScript in the browser.
Hyper-Threading Will Exacerbate Speculative Execution Flaws
We’ve seen over the past few months that the Meltdown and Spectre flaws were not a one-time vulnerability that we could patch once and then forget about. Multiple Spectre-like speculative execution flaws have been found since Meltdown and Spectre was revealed earlier this year, and chances are we’ll continue to see more of them until the entire class of speculative execution bugs are fixed at the CPU architecture level.
de Raadt also believes that Hyper-Threading itself will exacerbate most of the speculative execution bugs in the future, which is why now is the best time to disable it. He also recommended updating your BIOS firmware if you can.
The OpenBSD founder criticized Intel over not being very transparent about how it intends to fix these speculative execution flaws once and for all and also about not properly documenting which operating systems are supposed to do to mitigate these bugs. The OpenBSD team had to learn how to research and develop their own mitigations based on what other operating systems were doing without much help from Intel.
OpenBSD version 6.4 and newer will disable Hyper-Threading completely. However, versions 6.2 and 6.3, which may still be in production at certain companies, will not receive backported patches due to the amount of work that is required to fix these issues. Because of that, the OpenBSD founder recommended everyone to take responsibility for their own machines and disable Intel’s Hyper-Threading.
Intel's Stance
Intel's stance on this issue is that disabling Hyper-Threading is not required for protection if all other available mitigation strategies are employed, but may be advisable in a very small subset of scenarios where IT administrators or cloud providers cannot guarantee that all of their virtualized operating systems have been updated. The company previously said that non-virtualized environments should see a low degree of risk from the Foreshadow flaw if their systems are updated. However, many users may not be able to update their systems with Intel's microcode unless motherboard and laptop makers issue those updates to older systems too. Intel has also admitted that data center customers may need to take additional steps to protect themselves beyond simply updating their systems.
In reality, it's likely nobody can accurately say how small or large the risk of these flaws will be, because if they could, it wouldn't have taken 20 years to realize how dangerous the original Spectre bug could be. Ultimately, we'll all have to wait and see how effective the attackers will be in weaponizing these bugs. However, it's Intel and other chip makers' responsibility to ensure that their customers benefit from as much security as possible and are not left vulnerable to attacks.









