Linux users on Tuesday got a major dose of bad news—a 12-year-old vulnerability in a system tool called Polkit gives attackers unfettered root privileges on machines running most major distributions of the open source operating system.
Previously called PolicyKit, Polkit manages system-wide privileges in Unix-like OSes. It provides a mechanism for nonprivileged processes to safely interact with privileged processes. It also allows users to execute commands with high privileges by using a component called pkexec, followed by the command.
Trivial to exploit and 100 percent reliable
Like most OSes, Linux provides a hierarchy of permission levels that controls when and what apps or users can interact with sensitive system resources. The design is intended to limit the damage that can happen if a user isn’t trusted to have administrative control of a network or if the app is hacked or malicious.
Since 2009, pkexec has contained a memory-corruption vulnerability that people with limited control of a vulnerable machine can exploit to escalate privileges all the way to root. Exploiting the flaw is trivial and, by some accounts, 100 percent reliable. Attackers who already have a toehold on a vulnerable machine can abuse the vulnerability to ensure a malicious payload or command runs with the highest system rights available. PwnKit, as researchers are calling the vulnerability, is also exploitable even if the Polkit daemon itself isn’t running.
PwnKit was discovered by researchers from security firm Qualys in November and was disclosed on Tuesday after being patched in most Linux distributions. PwnKit is tracked as CVE-2021-4034.
In an email, Qualys Director of Vulnerability Threat Research Bharat Jogi wrote:
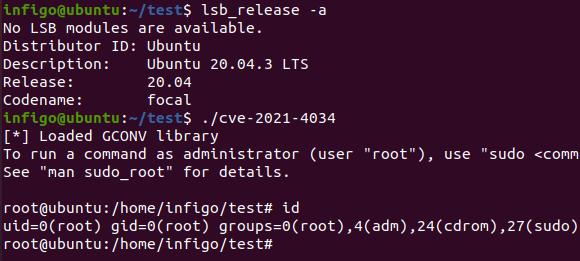
Jogi said exploits require local authenticated access to the vulnerable machine and can't be run remotely without such authentication. Here’s a video of the exploit in action.
For now, Qualys isn’t releasing proof-of-concept exploit code out of concern the code will prove more of a boon to black hats than to defenders. PoC code has been released by another source, and researchers said that it’s only a matter of time until PwnKit is exploited in the wild.
“We expect that the exploit will become public soon and that attackers will start exploiting it—this is especially dangerous for any multi-user system that allows shell access to users,” Bojan Zdrnja, a penetration tester and a handler at SANS, wrote. The researcher said he successfully recreated an exploit that worked on a machine running Ubuntu 20.04.
The Qualys researchers aren't the only ones to stumble upon this vulnerability, or at least a very similar bug. In 2013, researcher Ryan Mallon publicly reported much the same bug and even wrote a patch, although he ultimately could find no way to exploit the vulnerability. And last June, Github security researcher Kevin Backhouse also reported a privilege escalation vulnerability. It received the tracking designation of CVE-2021-3560 and a patch from major Linux distributors.
Major Linux distributors have released patches for the vulnerability, and security professionals are strongly urging administrators to prioritize installing the patch. Those who can’t patch immediately should use the chmod 0755 /usr/bin/pkexec command to remove the SUID-bit from pkexec, which prevents it from running as root when executed by a non-privileged user. Advisories from Debian, Ubuntu, and Red Hat are here, here, and here.
Those who want to know if the vulnerability has been exploited on their systems can check for log entries that say either “The value for the SHELL variable was not found the /etc/shells file” or “The value for environment variable […] contains suspicious content.” Qualys, however, cautioned people that PwnKit is also exploitable without leaving any traces.









